黑客偽造算力盜取多種數(shù)字貨幣
責(zé)編:gltian |2018-04-24 11:24:54經(jīng)過分析,我們發(fā)現(xiàn)此類攻擊利用了一個equihash算法(equihashverify: https://github.com/joshuayabut/equihashverify)實現(xiàn)上的邏輯漏洞。該漏洞可導(dǎo)致惡意礦工向z-nomp礦池提交虛假share,從而偽造自己的算力。從礦池中竊取誠實礦工的挖礦成果。由于目前許多新生數(shù)字貨幣均使用equihash算法進行工作量證明,且多數(shù)equihash礦池依賴于該equihashverify進行礦工算力校驗,所以該漏洞嚴(yán)重已經(jīng)影響多個數(shù)字貨幣礦池。
Equihash 是一種工作量證明算法,由 Alex Biryukov 以及Dmitry Khovratovich設(shè)計而成,以一種計算機科學(xué)以及加密學(xué)概念(叫做廣義生日悖論)為基礎(chǔ)。 Equihash是一種需要高內(nèi)存的工作量證明,這意味你能挖到多少幣主要取決于你的設(shè)備內(nèi)存的大小。在短期內(nèi)要創(chuàng)建一個低成本的挖礦定制硬件(專用集成電路)幾乎不可能,所以Equihash被認(rèn)為可以構(gòu)造更去中心化的一種POW算法。z-nomp在對Equihash工作量證明進行驗證的時候使用了equihashverify依賴庫來對礦工提交算力證明份額進行校驗。equihashverify對Equihash解驗證的錯誤實現(xiàn),導(dǎo)致了該漏洞。
下面我們來看看漏洞:
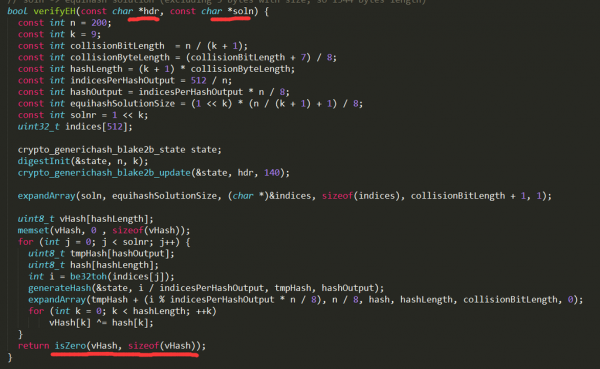
在equi.c文件中,在函數(shù)bool verifyEH(const char *hdr, const char *soln)中,hdr是區(qū)塊頭信息,參數(shù)soln是礦工求解出來的{Xij}序列。verifyEH函數(shù)的作用,就是用來判斷{Xij}是否是由區(qū)塊頭信息hdr產(chǎn)生的廣義生日悖論問題的正確解。
Equihash算法的整體實現(xiàn)可以理解為將Xij序列帶入到
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512);
然后判斷Vhash的結(jié)果是否全部為0。如果全部為0,則返回true;如果全部不為0,則返回false。這看似正確的實現(xiàn),但實際上編程人員沒有考慮到:在廣義生日悖論問題中,所有的xij必須是不相同的。而這里并沒有檢查是否由重復(fù)。對于任意區(qū)塊頭hdr,攻擊者只要讓所有的 xi全部相等,則得到結(jié)果:
hash(hdr,x1)=hash(hdr,x2) =…= hash(hdr,x512)
由于這里剛好有偶數(shù)個,那么可以得到:
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512)=0
也就是說,對于任意hdr,攻擊者隨機選擇一個21bit的數(shù)x,讓后讓soln={x,x,x,…,x},就可以繞過廣義生日悖論問題驗證,從而實現(xiàn)高達數(shù)十萬倍的算力數(shù)虛構(gòu)。由于equihashverify實現(xiàn)中缺乏equihash論文中的多種其他校驗算法,所以除了這個簡單的碰撞攻擊之外,該代碼還存在其他安全問題。密碼算法的實現(xiàn)應(yīng)嚴(yán)格按照算法標(biāo)準(zhǔn)來進行,否則就容易出現(xiàn)安全漏洞。Equihash算法標(biāo)準(zhǔn)詳細細節(jié)可參考論文:https://www.cryptolux.org/images/b/b9/Equihash.pdf
漏洞影響范圍
z-nomp是目前是目前市場占有率最高的equihash礦池。此次偽造算力攻擊主要針對各個z-nomp或基于z-nomp的礦池實例,至少影響了包括Zcash、Bitcoin Gold、Zencash、Bitcoin Private、Zclassic、Komodo、Hush、BitcoinZ、Bitcoin Candy、NewBTG等多種數(shù)字貨幣。
當(dāng)前修復(fù)情況
目前,z-nomp已經(jīng)將了equihashverify庫的的依賴換成了官方認(rèn)證的版本(https://github.com/zencashofficial/equihashverify.git)。zencash官方已在上周發(fā)布更新公告:https://blog.zencash.com/update-for-the-equihash-mining-application-z-nomp/。 Bitcoin Gold官方也更新了新的equihashjs-verify。Zclassic/BTG/Zcash等主流數(shù)字貨幣和主流礦場均已修復(fù)了該實現(xiàn)漏洞。但由于數(shù)字貨幣分叉幣和代碼fork非常多,所以仍存在眾多小數(shù)字貨幣和小礦池未修復(fù)該漏洞,360建議各數(shù)字貨幣社區(qū)和礦池及時更新。
解決方案
可使用目前zencash官方的equihash解校驗器的來進行廣義生日問題解校驗。https://github.com/zencashofficial/equihashverify
這里提供一個簡單的POC:
原文:https://www.anquanke.com/post/id/106025
- ISC.AI 2025正式啟動:AI與安全協(xié)同進化,開啟數(shù)智未來
- 360安全云聯(lián)運商座談會圓滿落幕 數(shù)十家企業(yè)獲“聯(lián)營聯(lián)運”認(rèn)證!
- 280萬人健康數(shù)據(jù)被盜,兩家大型醫(yī)療集團賠償超4700萬元
- 推動數(shù)據(jù)要素安全流通的機制與技術(shù)
- RSAC 2025前瞻:Agentic AI將成為行業(yè)新風(fēng)向
- 因被黑致使個人信息泄露,企業(yè)賠償員工超5000萬元
- UTG-Q-017:“短平快”體系下的高級竊密組織
- 算力并網(wǎng)可信交易技術(shù)與應(yīng)用白皮書
- 美國美中委員會發(fā)布DeepSeek調(diào)查報告
- 2024年中國網(wǎng)絡(luò)與信息法治建設(shè)回顧