IPv6的ACL配置及注意點(diǎn)
責(zé)編:admin |2015-01-21 11:14:53IPv6ACL規(guī)則如下:
1 只能使用命名的ACL
2 ACL序號(hào)匹配由小到大
3 默認(rèn)情況下,隱含permit icmp any any nd-na 和permit icmp anyany nd-ns 用于鄰居發(fā)現(xiàn)協(xié)議的鄰居通告和鄰居請(qǐng)求,允許接口發(fā)送和接收IPv6鄰居發(fā)現(xiàn)包。
3 結(jié)尾默認(rèn)隱含 deny ipv6 any any
4 使用命令ipv6 traffic-filter應(yīng)用于接口的in or out方向
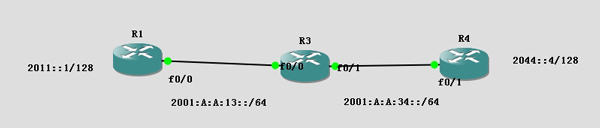
需求:在R1配置ACL,禁止R1的環(huán)回接口訪問(wèn)R4的環(huán)回接口地址;
ACL配置如下,其它配置略:
R1(config)#ipv6 access-list Mao
R1(config-ipv6-acl)#deny 2011::1/1282044::4/128
R1(config-ipv6-acl)#permit any any
R1(config)#int fa0/0
R1(config-if)#ipv6 traffic-filter Mao out
R1#show ipv6 access-list
IPv6 access list Mao
deny ipv6 host 2011::1 host 2044::4 sequence 10
permit ipv6 anyany sequence 20
R1#ping 2044::4 source 2011::1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2044::4,timeout is 2 seconds:
Packet sent with a source address of2011::1
!!!!!
Success rate is 100 percent (5/5),round-trip min/avg/max = 24/36/52 ms
為什么會(huì)ping通呢?是因?yàn)槊頸pv6 traffic-filter的作用是過(guò)濾路由器轉(zhuǎn)發(fā)的流量,但不過(guò)濾源自本路由器的流量;
現(xiàn)在將ACL進(jìn)行修改如下,拒絕從R4環(huán)回接口發(fā)回來(lái)的數(shù)據(jù)包,并將ACL應(yīng)用至fa0/0的入接口方向上;
R1(config)#ipv6access-list Mao
R1(config-ipv6-acl)#no deny ipv6 host 2011::1 host 2044::4
R1(config-ipv6-acl)#deny ipv6 2044::4/128 2011::1/128
R1(config-ipv6-acl)#permit any any
R1(config-if)#no ipv6 traffic-filter Mao out
R1(config-if)#ipv6 traffic-filter Mao in
R1#ping2044::4 source 2011::1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2044::4,timeout is 2 seconds:
Packet sent with a source address of2011::1
…..
Success rate is 0 percent (0/5)
R1#show access-lists
IPv6 access list Mao
deny ipv6 host 2044::4 host 2011::1 (5 matches) sequence 30 //匹配了5個(gè)數(shù)據(jù)包
permit ipv6 anyany (4 matches) sequence 40
總結(jié):命令ipv6traffic-filter不過(guò)濾源自本路由器的流量,因此在配置IPv6 ACL時(shí)需要注意流量的起源是否來(lái)至本路由器。
以上例子也可以在R3上配置,如下:
R3(config)#ipv6access-list Mao
R3(config-ipv6-acl)#deny ipv6 2011::1/128 2044::4/128
R3(config-ipv6-acl)#permit any any
R3(config)#int fa0/1
R3(config-if)#ipv6 traffic-filter Mao out
R1#ping 2044::4 source 2011::1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2044::4,timeout is 2 seconds:
Packet sent with a source address of2011::1
SSSSS
Success rate is 0 percent (0/5)
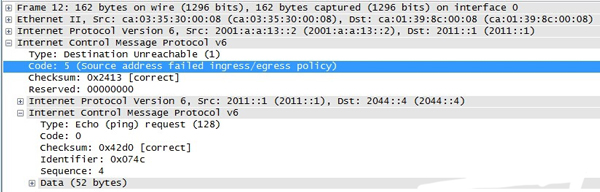
不通,在R1和R3之間抓包可知,如下圖:
的類(lèi)型為1,表示目標(biāo)不可達(dá),代碼字段為5,源地址被入站/出站策略所阻止。
- ISC.AI 2025正式啟動(dòng):AI與安全協(xié)同進(jìn)化,開(kāi)啟數(shù)智未來(lái)
- 360安全云聯(lián)運(yùn)商座談會(huì)圓滿落幕 數(shù)十家企業(yè)獲“聯(lián)營(yíng)聯(lián)運(yùn)”認(rèn)證!
- 280萬(wàn)人健康數(shù)據(jù)被盜,兩家大型醫(yī)療集團(tuán)賠償超4700萬(wàn)元
- 推動(dòng)數(shù)據(jù)要素安全流通的機(jī)制與技術(shù)
- RSAC 2025前瞻:Agentic AI將成為行業(yè)新風(fēng)向
- 因被黑致使個(gè)人信息泄露,企業(yè)賠償員工超5000萬(wàn)元
- UTG-Q-017:“短平快”體系下的高級(jí)竊密組織
- 算力并網(wǎng)可信交易技術(shù)與應(yīng)用白皮書(shū)
- 美國(guó)美中委員會(huì)發(fā)布DeepSeek調(diào)查報(bào)告
- 2024年中國(guó)網(wǎng)絡(luò)與信息法治建設(shè)回顧