基于JXWAF快速搭建釣魚網(wǎng)站
責(zé)編:gltian |2018-04-23 10:57:14一、前言
前段時間為了加強(qiáng)內(nèi)部安全意識,需要進(jìn)行釣魚郵件演練,于是通過JXWAF快速搭建了一個釣魚網(wǎng)站,發(fā)現(xiàn)效果不錯,特此分享。
PS:本文僅用于技術(shù)討論及分享,嚴(yán)禁用于非法用途
二、規(guī)則配置
首先假設(shè)攻擊場景為獲取公司內(nèi)部OA賬號,內(nèi)部OA域名為oa.testing.com。那么第一步就是注冊域名,比如去萬網(wǎng)注冊釣魚域名oa.testlng.com,地址指向為釣魚網(wǎng)站IP地址。
為了方便這里以DVWA來當(dāng)成OA進(jìn)行演示。
先來分析登陸成功和登陸失敗的特征。
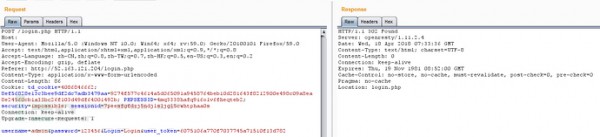
登陸失敗。
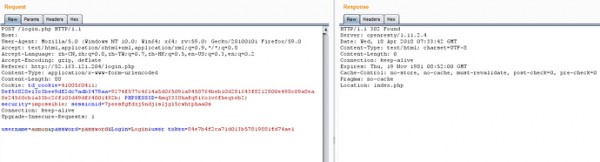
登陸成功。
如圖,登陸失敗和登陸成功的區(qū)別在于response中Location的指向,失敗指向為login.php,成功指向為index.php,那么我們就以此為特征來設(shè)置兩條規(guī)則,一條識別登陸失敗的賬號,一條來識別登陸成功的賬號,當(dāng)然也可以不用這么精細(xì),直接設(shè)置規(guī)則記錄輸入的賬號密碼。
分析結(jié)束,接下來是搭建JXWAF及配置規(guī)則,搭建可以參考 https://github.com/jx-sec/jxwaf,規(guī)則配置如下:
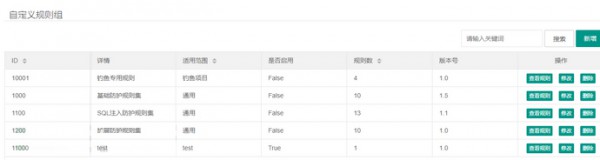
登陸JXWAF,在自定義規(guī)則組中新建規(guī)則組 “釣魚專用規(guī)則”。
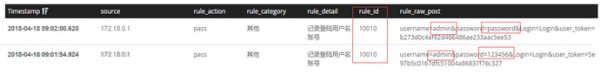
先來設(shè)置第一條規(guī)則(不建議用這種方式),無論登陸成功失敗直接記錄輸入賬戶密碼,這是釣魚網(wǎng)站通常的做法,因為他們沒有用戶數(shù)據(jù)庫,也就只能這么處理了。規(guī)則配置如下,比較簡單。
結(jié)果如下:
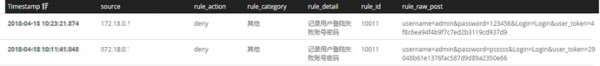
設(shè)置第二條規(guī)則,只有驗證用戶名密碼失敗時才記錄(不截圖直接放規(guī)則)。
{
??? "rule_action": "deny",
??? "rule_category": "其他",
??? "rule_update_category": "resp",
??? "rule_log": "true",
??? "rule_serverity": "high",
??? -
??? "rule_matchs": [
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "URI"
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "login.php$",
??????????? "rule_negated": "false"
??????? },
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "REQUEST_METHOD"
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "POST",
??????????? "rule_negated": "false"
??????? },
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "RESP_HEADERS",
??????????????????? -
??????????????????? "rule_specific": [
??????????????????????? "Location"
??????????????????? ]
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "index.php$",
??????????? "rule_negated": "false"
??????? }
??? ],
??? "rule_id": "10012",
??? "rule_detail": "記錄用戶登陸成功賬號密碼"
}
結(jié)果如下:
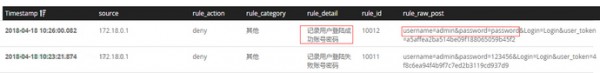
設(shè)置第三條規(guī)則,只有驗證用戶名密碼成功時才記錄(不截圖直接放規(guī)則)。
{
??? "rule_action": "deny",
??? "rule_category": "其他",
??? "rule_update_category": "resp",
??? "rule_log": "true",
??? "rule_serverity": "high",
??? -
??? "rule_matchs": [
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "URI"
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "login.php$",
??????????? "rule_negated": "false"
??????? },
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "REQUEST_METHOD"
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "POST",
??????????? "rule_negated": "false"
??????? },
??????? -
??????? {
??????????? -
??????????? "rule_transform": [
??????????????? "none"
??????????? ],
??????????? -
??????????? "rule_vars": [
??????????????? -
??????????????? {
??????????????????? "rule_var": "RESP_HEADERS",
??????????????????? -
??????????????????? "rule_specific": [
??????????????????????? "Location"
??????????????????? ]
??????????????? }
??????????? ],
??????????? "rule_operator": "rx",
??????????? "rule_pattern": "index.php$",
??????????? "rule_negated": "false"
??????? }
??? ],
??? "rule_id": "10012",
??? "rule_detail": "記錄用戶登陸成功賬號密碼"
}
結(jié)果如下:
三、總結(jié)
只需花幾分鐘時間配置規(guī)則即可實現(xiàn)釣魚網(wǎng)站的搭建,因為是通過jxwaf反向代理到真實的目標(biāo)網(wǎng)站地址,所以整個釣魚網(wǎng)站,除了域名外其他都跟實際網(wǎng)站是一致的,隱蔽性比起自建的釣魚網(wǎng)站更強(qiáng),也更不容易引起攻擊目標(biāo)的警覺。在釣魚演練過程中發(fā)現(xiàn),當(dāng)有些用戶反映過來時候,會通過XSS攻擊,SQL注入等方式嘗試反X釣魚網(wǎng)站,所以這種方式的另一好處就是安全,因為攻擊流量都導(dǎo)入真實網(wǎng)站去了,就是被成功攻擊也是真實網(wǎng)站的事情,釣魚網(wǎng)站在這個過程中全程打醬油。 而且在釣魚過程中會有些用戶故意”搗亂”,或者是謹(jǐn)慎的先嘗試錯誤的密碼看網(wǎng)站是不是都返回正確登陸,那么通過這種方式會使得釣魚過程更真實,同時獲取用戶的輸入數(shù)據(jù)也是真實的,方便事后統(tǒng)計結(jié)果。
本文轉(zhuǎn)自FreeBuf.COM
- ISC.AI 2025正式啟動:AI與安全協(xié)同進(jìn)化,開啟數(shù)智未來
- 360安全云聯(lián)運(yùn)商座談會圓滿落幕 數(shù)十家企業(yè)獲“聯(lián)營聯(lián)運(yùn)”認(rèn)證!
- 280萬人健康數(shù)據(jù)被盜,兩家大型醫(yī)療集團(tuán)賠償超4700萬元
- 推動數(shù)據(jù)要素安全流通的機(jī)制與技術(shù)
- RSAC 2025前瞻:Agentic AI將成為行業(yè)新風(fēng)向
- 因被黑致使個人信息泄露,企業(yè)賠償員工超5000萬元
- UTG-Q-017:“短平快”體系下的高級竊密組織
- 算力并網(wǎng)可信交易技術(shù)與應(yīng)用白皮書
- 美國美中委員會發(fā)布DeepSeek調(diào)查報告
- 2024年中國網(wǎng)絡(luò)與信息法治建設(shè)回顧